The Hidden Psychology of Cybersecurity
Unlocking the Behavioral Triggers Behind Security Breaches
Introduction
There is a myth that ostriches bury their heads in the sand to avoid danger. This is known as Ostrich Syndrome or Ostrich Effect and refers to the tendency of knowingly or unknowingly avoiding potentially negative or difficult, but useful, decisions. This avoidance is driven by a desire to avoid psychological discomforts.
During World War II, the Allied forces analyzed the aircrafts that made it back safely. They observed that there were bullet holes in the returning aircrafts, and these bullet holes were concentrated on the fuselage, outer wings, and tail of the planes that returned safely. The obvious conclusion was to reinforce these heavily damaged areas with additional armor. However, Hungarian mathematician Abraham Wald identified a critical flaw in this reasoning, now known as survivorship bias. He pointed out that the military was only examining planes that survived and returned; planes that were hit in other areas and lost were not part of the data. Therefore, the areas with few or no bullet holes on returning planes—such as the engines, cockpit, and fuel tanks—were the most vulnerable. This counterintuitive conclusion helped the military improve aircraft survivability by protecting the most vulnerable parts rather than the most visibly damaged parts on surviving planes.
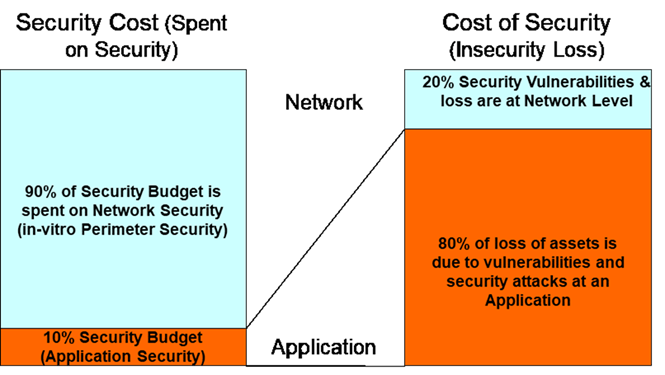
In Cybersecurity all CISO (Chief Information Security Officer) are victim of both ostrich syndrome and survivorship biases. They are ignoring the most vulnerable regions of the cyberspace. The money spent on security can be split into two distinct areas, namely “Security Cost” and “Cost of Security”. Security cost is the cost incurred by a company to ensure security whereas cost of security is the cost or loss due to insecurity or lack of security within the corporation. About 90% of the money is spent on security is related to network or perimeter security. However, the insecurity part of an organization is the victim of survivorship bias and ostrich effect. Simply because they are not visible or tangible. There is no inventory of the software assets in an organization. This includes software assets created by inhouse IT teams and the software obtained from outside sources like external vendors or open-source software products and libraries.
NIST (National Institute of Standards and Technology), in the US maintains a comprehensive cybersecurity vulnerability database called National Vulnerability Database. National Vulnerability Database includes three databases namely, CVE (Common Vulnerabilities and Exposures), CPE (Common Platform Enumeration), and CWE (Common Weakness Enumeration) that are crucial components of cybersecurity, working together to identify, classify, and address vulnerabilities. CVE is a dictionary that assigns unique identifiers to publicly known security flaws. CPE is a structured naming system for IT systems, software, and packages, allowing for consistent identification of vulnerable products. CWE is a catalog of software weakness types, providing a standardized way to classify vulnerabilities. These databases need to be integrated with the software assets database of the organization.
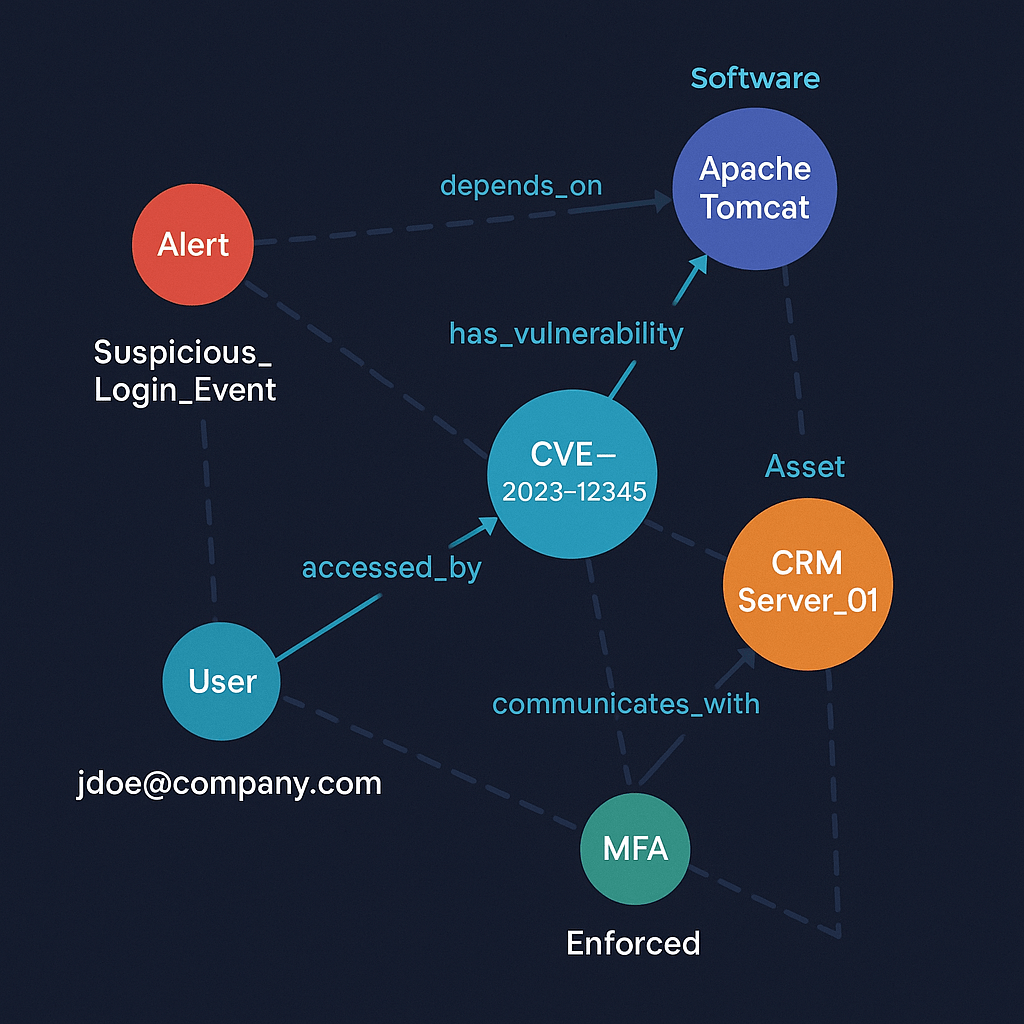
In the automobile industry, a car is recalled based on defective parts. Recall occurs when a manufacturer or the National Highway Traffic Safety Administration (NHTSA) identifies a safety defect or non-compliance with safety standards in a vehicle or its components. To ensure successful recalls, the car manufacturers maintain the bill of material of every manufactured car. Similarly, to minimize the cost of security every organization needs to maintain the Hardware & Software Bill of Material (SBOM). We at BlueRose integrate all these vulnerability databases like VCE, CPE, and CWE integrate with the organizational hardware and software assets and software/hardware bill of material to construct a Cybersecurity Cognitive Graph.
At BlueRose we offer comprehensive cybersecurity to our customers. We create Cybersecurity Cognitive Graphs that offer comprehensive cybersecurity using the organizational assets, SBOM, vulnerability databases, and Attack Intelligence. Like an automobile recall, the attack intelligence combined with cognitive graph can immediately alert the user about the security holes and recovery processes.





